Cybersecurity: Assuring the future of organizations in the post-COVID era
The increase in Cyberattacks incidents is common in times of crises and 2008’s worldwide economic recession is the most recent proof. From Heartland’s biggest credit card scam in history to Virginia’s prescription monitoring hack, the 2008 economic recession has witnessed a considerable increase in breaches and cybercrimes. As recorded by the Financial Fraud Action (UK), online banking fraud was peaking in 2009 at £59.7 million before falling in 2011 to £35.4 million. While it is remarked that history repeats itself, the COVID-19 era is no exception.
Today’s reality is dominated by remote work that introduced businesses to a new level of dependency on digital collaboration tools. In this context, while authorities focused their efforts mainly on fighting the spread of the virus and improve their healthcare systems, IT professionals are concerned about assuring the environments’ security during this transition. In fact, based on Fugue’s survey on the state of cloud security published in April 2020, 84% of security professionals are worried that their institution has already faced a breach during the transition. This explains why despite the worldwide decline in job opening, countries such as the US and UK saw a rise in requests for information security roles.
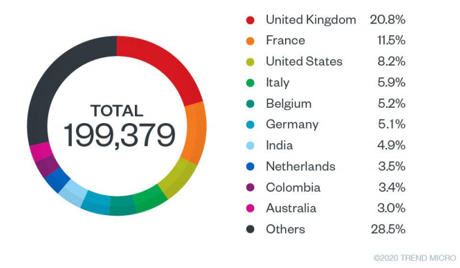
In terms of numbers, reported cybercrimes are already registering a steep rise and unprepared tools have experienced some of the world’s biggest breaches. ZOOM, the videotelephony software program, had 500,000 personal URLs and information sold on the dark web. Also, a hacker sold 115M personal data belonging to customers of a Pakistani mobile operator for $2.1M in bitcoin. These are just examples of breaches that can severely affect the public. From the visible side of the iceberg, the Internet Crime Complaint Center of the FBI announced a 300% increase in registered cybercrimes in five months, that jumped from 1,000 to 3,000 complaints per day. Additionally, the US Department of Health and Human Services stated that there have been 132 breaches this year (February to May) which is an equivalent of almost 50% increase compared to last year’s reported cases. Google, from its end, is currently preventing, over 18M COVID-19 related email scams and 240M spam messages on a daily basis. As Trend Micro confirms, malicious spam emails are the most considerable share of cyberattacks (up to 65.7%) and the top countries targeted by these types of hacks from January to March 2020 are mainly European countries with the UK at the top (20.8%), in addition to the United States and India.
Experts predicted in December 2019 that security spending would experience a growth of 8.7%. However, the pandemic urged Gartner to adapt its estimate to 2.4% growth. Albeit the decline in the expected growth, factors related to the current businesses’ development are in favor of few security market segments such as cloud- and SaaS-based solutions that will still drive the sector on a positive trend. In fact, only Network security equipment and consumer security software are expected to decrease (-12.6% and -0.3%), while a considerable high increase of 33.3% is predicted for Cloud Security. The 2020 market will also experience 7.2% growth for data security, 6.2% for Application security, and 5.8% for both Identity access management and Infrastructure protection.
From a cost viewpoint, IBM security’s latest insights reported that 2020 Cyber-attacks’ average total cost of a breach remains slightly at the same level ($3.86M in 2020 for $3.9M in 2019), with major increases targeting the energy (14.1% increase) and healthcare (10.5% increase) sectors. In fact, as countries’ stability is highly depending on the energy and utility industries, these sectors became in the past years a prime target for cyber-attacks encouraged by specific political and economic aims. Concerning the Healthcare sector, ForgeRock’s 2019 Consumer Breach report is showing that the most targeted data types are social security numbers, followed by medical records. These breaches will continue to increase as more COVID-19 tests and treatments are conducted.
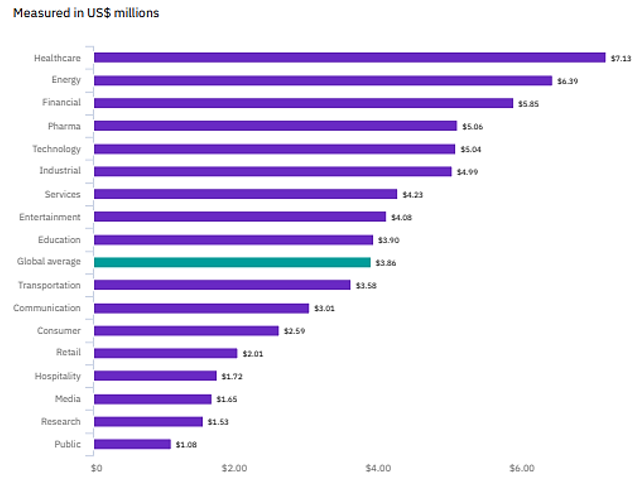
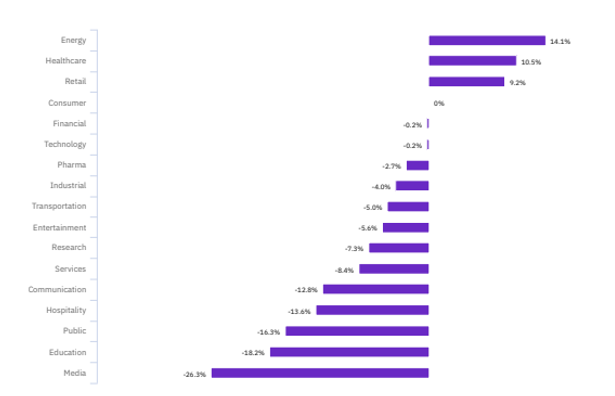
Source: IBM Security, “Cost of Data Breach Report 2020”.
What about African countries?
The submerged side of the iceberg is mainly hiding the African countries’ situation as the cases are rarely covered. Moreover, their contribution to the cybersecurity market is still considerably low, while the number of incidents, mainly related to personal data security, is rising. Tomiwa Ilori highlighted in his paper published in June 2020 that out of the 54 African countries only 28 proved to have a data protection law including Morocco, Mauritius, Kenya, Uganda, Senegal, Tunisia, South Africa, and Nigeria.
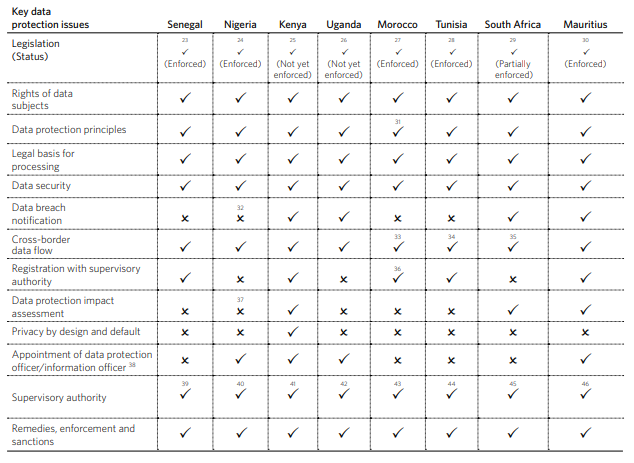
The provided snapshot above emphasizes that for African countries, there will only be room for serious discussions about Cybersecurity solutions when the inadequacy of their data collection’s regulation framework will be tackled. Raising the countries to the current Cybersecurity reality requires at first protecting the organizations’ most important asset by enhancing regulation and compliance requirements. To achieve this, data protection laws are only the first step. In this context, access to international instruments to reduce compliance gaps becomes a must. The continent should welcome, and particularly during this crisis, partnership opportunities between the different stakeholders, aiming to elevate their data protection laws to combine them with their cybersecurity strategies.
Nada Benslimane – Business Analyst
Sources:
https://www.ibm.com/security/digital-assets/cost-data-breach-report/#/
https://www.imcgrupo.com/covid-19-news-fbi-reports-300-increase-in-reported-cybercrimes/
https://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
https://www.power-eng.com/2020/02/12/energy-sector-cybersecurity-is-vulnerable-but-achievable/#gref
https://healthitsecurity.com/news/health-sector-most-targeted-by-hackers-breach-costs-rise-to-
You may also like
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235
Warning: Undefined variable $content in /var/www/sdomains/nexatestwp.com/infomineo.nexatestwp.com/public_html/wp-content/themes/infomineo/single.php on line 235